Public Key Cryptography
On the Internet, innumerable people and machines communicate with each other via network infrastructures. The secured identity of a participant is ensured by the respective use of an individual, unique and secret Key. Depending on the purpose, symmetric or asymmetric encryption methods can be used. The central problem with both methods is the secure exchange of keys between the participants, which usually takes place online and not in a face-to-face meeting.

Public Key Cryptography solves this problem by allowing each partner to simply publish its public key. This generates a pair of keys that belong together, a so-called public key and its corresponding private key. The public key is public and enables encryption of data that can only be decrypted with the corresponding private key. In addition, the public key can be used to verify digital signatures generated with the private key.
The signature ensures that the data actually originates from the corresponding sender and has been sent unaltered. This signature therefore verifies that the content of the file has not been modified. However, the question of how to know that a particular public key is actually assigned to a particular person remains unsolved. This problem of key distribution with unique identities is solved by a PKI.
PKI (Public Key Infrastructure)
Public Key Cryptography is based on a variety of methods that are suitable for securing the online exchange of keys. With increasing complexity, diversity and number of participants, it quickly reaches its limits.
A PKI (Public Key Infrastructure) solves the problem by creating the basis for public key cryptography to become scalable and trustworthy. The core of a PKI are the certificates issued by the so-called Certification Authority (or Certificate Authority, CA for short). The assignment of the public key to an entity (human or machine) takes place via a so-called X.509 certificate. Each participant receives such a certificate from the PKI that forms the trust anchor in the respective network.
A certificate contains all the information relevant for secure data exchange (including the public key or certain authorizations of the participants). It is used as a verified and approved identification card (user certificate) for the communicating participants of the network.
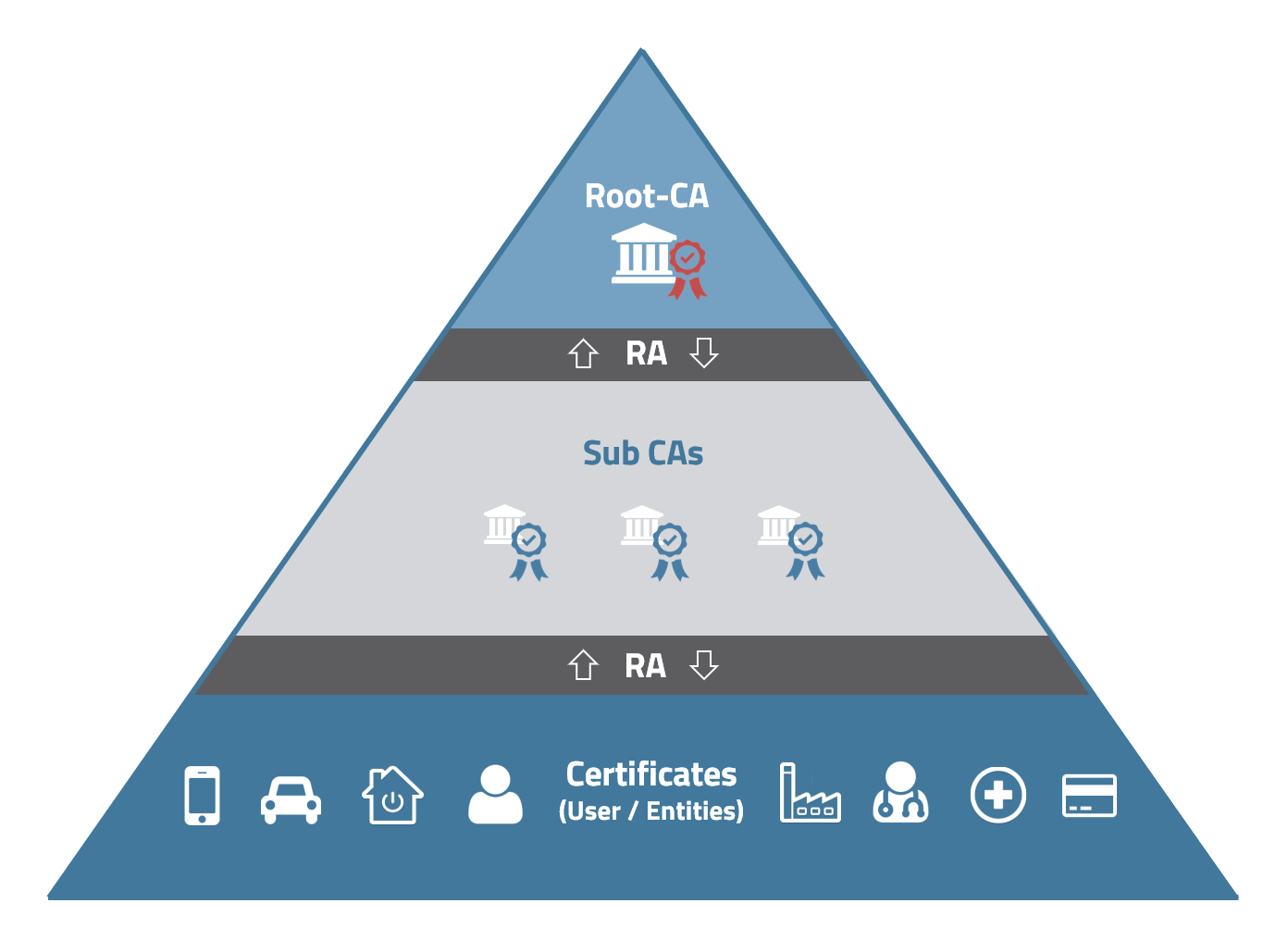
Structure of the authorities of a PKI (© MTG)
A Public Key Infrastructure follows the logical structure of a pyramid. The top entity is the so-called Root Certification Authority (Root CA). This authority signs one or more subordinate Sub Certificate Authorities (Sub CAs for short) with its private key. This verifies that the certificate-issuing authority, the sub-CA, is trustworthy. A root CA is rarely used in operation, but it contains very sensitive key material. For this reason, it is normally operated "offline". It only becomes "active" when, for example, certificates of the sub CAs are renewed or new sub CAs are set up within the PKI.
The Registration Authority (RA in short) manages the certificates of the PKI and takes over the checking and management of application data and for forwarding it to the Sub CA or Root CA. The RA software can perform the verification and approval process automatically (e.g., when certificates for a large number of IoT devices are involved). In certain cases, the approval process can also be checked in first by authorized entities and then the certificate generation can be triggered manually via the software.
The PKI platform MTG CARA provides all the functions required for issuing, distributing and verifying digital X.509 and CV certificates. In addition to the CA functionality, all the functions of a Registration Authority (RA) are already integrated.
Operation of PKIs
PKIs can be operated in different ways, depending on the purpose. For standard use cases that require few adjustments, certificates can be obtained from PKI service providers, for example. For more extensive use or for special use cases, own PKIs can be considered. These can then be operated in the company's own data center (on premise) or obtained as a service from specialized cloud service providers. MTG supplies PKI solutions that are specially adapted to the customer's requirements and can be operated flexibly either on-premise or in a cloud environment.


