PQC – Post-Quantum Cryptography
Post-Quantum Cryptography (PQC) is the field of cryptography that deals with cryptographic primitives and algorithms designed to protect against attacks from quantum computers. In recent years, this topic has already received a great deal of attention from researchers. The industry, however, is just starting to approach the topic.
Quantum computers &
Quantum mechanical principles

A quantum computer operates on the basis of the quantum mechanical principles superposition and quantum entanglement. The unit of information in a quantum computer is called qubit. In contrast to classical bits, which either have the value 1 or 0 and are therefore in one state or the other, a qubit is a superposition of these states. This means that it is both 0 and 1 at the same time and assumes both states. The phenomenon of quantum entanglement is the second principle of quantum mechanics that applies to qubits. This principle allows qubits to interact and influence one another regardless of the distance and medium between them.
Combined with other properties of quantum computers, these principles make it possible to calculate specific problems much more efficiently than with conventional computers. The main advantage of a quantum computer is its ability to simulate the physical micro-world much more accurately. As our world is governed by quantum mechanics at atomic level, a computer that understands and uses these same phenomena can much better approximate quantum behaviors than a traditional computer.
Research on quantum computers has gained much traction in recent years. With a quantum computer, it is much faster to run simulations and perform certain calculations. Therefore, it can be used to optimize various applications and products in the pharmaceutical, chemical, and other industries. A rather negative side effect of quantum computers is their ability to solve the mathematical problems on which today's cryptography is based very efficiently.
Why do companies need to start dealing with PQC today?
According to experts, commercial quantum computers will very likely be available by the end of the next decade. This seems apparently still a long way off in the future, especially since it seems reasonable for company managements to wait for the envisaged NIST standardization procedures for PQC algorithms.
However, this strategy bears risks, because PQC is already relevant today, especially for long-lived products and critical infrastructures. Applications that exchange date with asymmetric encryption methods are particularly affected. With RSA or ECC encrypted data that is recorded today will be easy to decrypt in the future thanks to quantum computers. This means that considerable damage can be caused in retrospect. An attractive business model for hackers could be to store encrypted data today and to sell it in the future. “Store Now, Decrypt Later” (SNDL) activities are thus serios threats for companies and organizations.
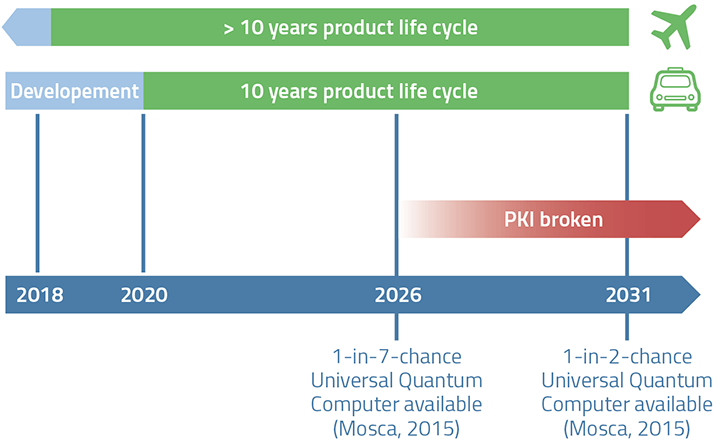
A car developed and sold in this decade is very likely to be exposed to unprotected new attack risks during its operational lifetime.
As soon as long-lived products and services run into the quantum computing era with current encryption methods, it will be too late for companies to act in time.
Quantum-Safe
For this reason, decision-makers from relevant industries need to take appropriate action today to protect against future threats from quantum computers. Affected industries include:
- Transportation (e.g., automotive industry, railroad operations, airports)
- Energy supply (e.g., power plant operation, grid operation),
- Public authorities (e.g., police, military, government, judiciary),
- Research & development (e.g., high-tech companies, government research institutions).
In particular, the industries listed above should waste no time in becoming quantum safe to protect themselves from potential quantum computing attacks at an early stage.
Standardization
Standardization of PQC systems is an essential step towards a more secure, reliable and widely used post-quantum cryptography. Leading institutions such as ETSI, ITU-T, IETF and NIST have already started various standardization processes, but the final results are not expected for several years.
NIST, the National Institute of Standards and Technology in the U.S., issued a call for proposals in 2016 for cryptosystems that are secure against quantum computing. The submitted algorithms will be evaluated and some of them will be standardized. There were a large number of proposals submitted. In the meantime, few finalists and alternative candidates have made it to the next selection rounds.
The European standards organization ETSI has also started research in this area and published some preliminary reports
In addition, the IETF (Internet Engineering Task Force) has already published a standard for the post-quantum hash-based signature scheme XMSS (eXtended Merkle Signature Scheme) and plans to publish further standards soon.
Standardization of further PQC procedures will therefore take time, and it will be years before the international community implements these standards. Until then, MTG relies on high-security, hash-based algorithms such as XMSS and SPHINCS+ for signature operations and on the code-based Classic McEliece method for asymmetric public-key encryption and key exchange. Both algorithms are currently among the finalists in the NIST selection process. MTG regularly monitors new developments and evaluates new procedures on an ongoing basis.
Importance of
Crypto Agility & Hybrid Schemes
Against this background, a central aspect of the PQC development process is so-called crypto-agility. This is the ability to add and exchange cryptographic algorithms to and from products with minimal effort and downtime.
Hybrid techniques are another important aspect of PQC software development. They are highly recommended to ease the transition into the post-quantum era. A hybrid procedure is a combination of a traditional and a post-quantum procedure, which means that the resulting procedure is at least as secure as either of the two procedures used. In the key exchange example, this would mean that two independent key exchange procedures are performed, one using a traditional procedure such as Diffie-Hellman and one using a post-quantum procedure. The two resulting keys are then combined to create the final secret key that is exchanged.
Downloads & Links
Flyer MTG PQC - Post-Quantum Cryptography
MTG PQC - free Demo portal
Post Quantum Cryptography sichert die Security-Zukunft (de)
Post-Quantum-Sicherheit: Heute mitdenken – morgen profitieren (de)
Sind wir sicher? Kryptoagil gegen hackende Quantencomputer (de)
More Information on NIST & PQC
More Information on ETSI & PQC
More Information on IETF & PQC


