Digital Operational Resilience Act
DORA refers to EU Regulation 2022/2554 on digital operational resilience in the financial sector (the Digital Operational Resilience Act). The regulation was published on December 27, 2022, entered into force on January 17, 2023, and will be applied from January 17, 2025. In Germany, DORA will be implemented as part of the Financial Market Digitalization Act (FinmadiG), which was published as a government draft in December 2023 and, in addition to DORA, also includes the EU Money Transfers Regulation and the Markets in Crypto-Assets Regulation (MiCAR).
MTG ERS® solutions for encryption according to DORA (© MTG AG)
The MTG ERS platform provides the companies affected by DORA with a central system for all cryptographic tasks.
DORA aims to strengthen the resilience of the European financial market to cyber risks and security incidents.
DORA consolidates existing regulations across the EU:
- EBA Directive on ICT and security risk management (BAIT)
- TIBER-EU (TIBER-DE) from European Central Bank (ECB)
- NIS2 Directive (IT Security Act)
- Resilience of critical infrastructure (KRITIS Umbrella Act)
For example, the reporting process will be merged, and the financial supervisory authority BaFin in Germany will become the national reporting hub for security incidents in the financial sector.
The scope of DORA includes credit institutions, investment firms, providers of crypto services, and insurance companies.
Requirements for MTG ERS
The MTG ERS product range consists of several coordinated modules that help meet DORA's requirements (the Digital Operational Resilience Act). The MTG ERS platform provides companies affected by DORA with a centralized system for managing all cryptographic tasks. Thanks to secure identities and cryptographic keys, sensitive company processes can be secured across the entire key and certificate lifecycle.
We offer our customers attractive managed and customized on-premise solutions, and we are available to support you.
Legal requirements & schedule
The requirements of DORA are specified by regulatory technical standards (RTS) and implementation standards (ITS), which are jointly developed by three European supervisory authorities (EU Securities and Markets Authority, EU Banking Authority, and EU Insurance and Occupational Pensions Authority). Only some of the final RTS and ITS documents have currently been published. The remaining standards will follow in the course of 2024.
The DORA requirements can be roughly divided into the following categories:
- Risk management framework
- Classification and reporting of incidents
- Standards for testing digital resilience
- Management of third-party risk (service providers and outsourcing)
- Exchange of cyber threat data
The implementation of DORA brings major challenges for companies in the financial sector. On one hand, this is due to the scope of the task involved. On the other hand, there is a short period of time that companies have to implement the requirements. There is less than a year between the publication of the last RTS and ITS documents and the DORA application date, available for analysis, planning, and implementation.
MTG offers customers in the financial sector both managed cloud services and on-premise solutions. This offering is combined with direct access to excellent IT security expertise, which is required to plan and implement the security modules.
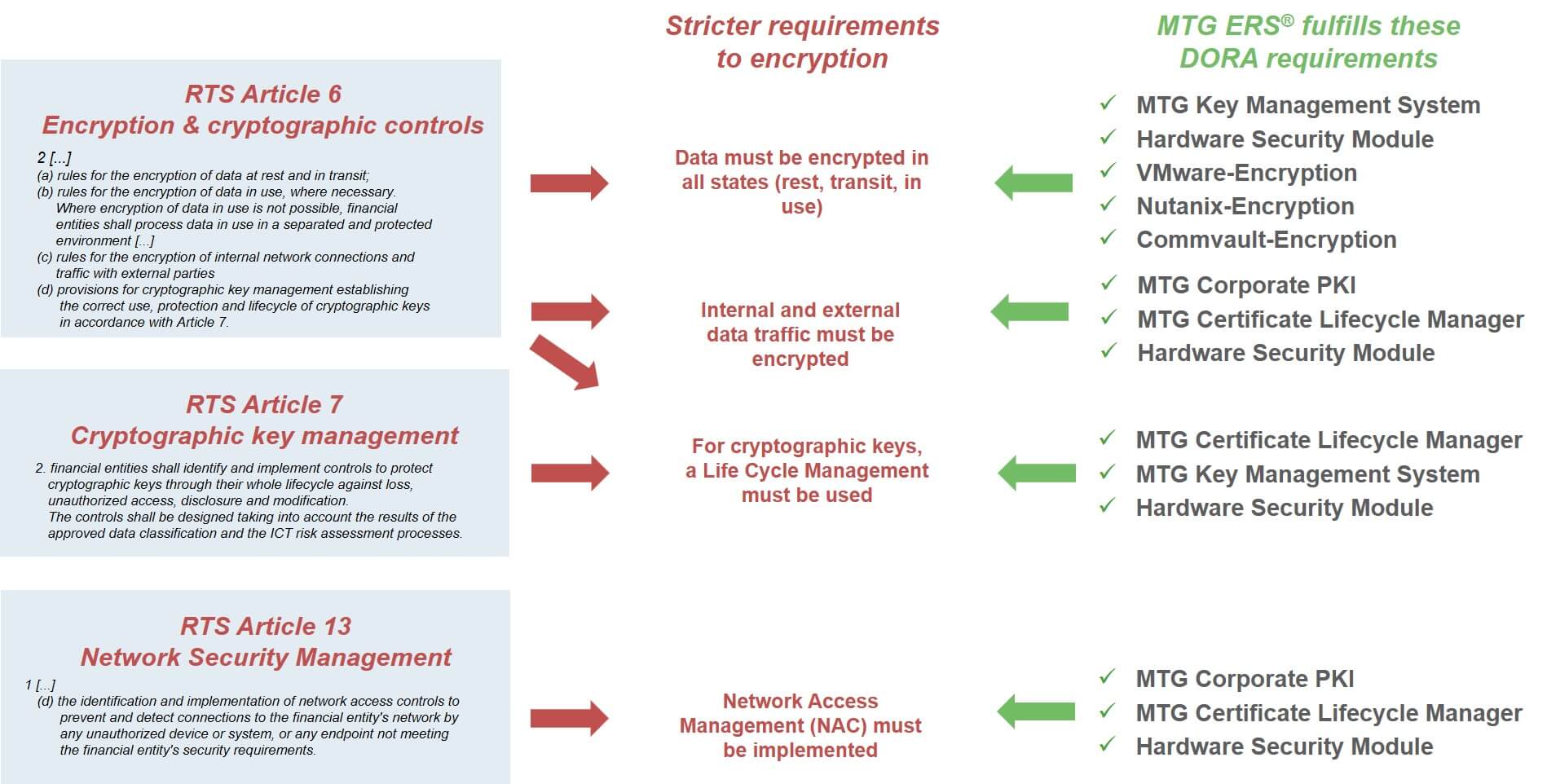
Article 7 of the Regulatory Standard (RTS) JC 2023 86 defines requirements for managing the cryptographic keys used, which can be implemented with the MTG ERS components. The MTG ERS solution is characterized by the ability to implement the requirements for key management, certificate lifecycle management, and PKI via a uniform, central system.
|
Request from the RTS |
Solution from MTG ERS |
|---|---|
|
Financial entities shall lay out in the provisions on cryptographic key management referred to in Article 6(2) point (d), the requirements for managing cryptographic keys through their whole lifecycle, including generating, renewing, storing, backing up, archiving, retrieving, transmitting, retiring, revoking and destroying keys. |
The central management of cryptographic keys and identities is the core function of all ERS products from MTG AG. They can be used to keep an overview of a company's cryptographic keys and protect them throughout their entire lifecycle. Organizational processes for key management can thus be easily mapped. |
|
Financial entities shall identify and implement controls to protect cryptographic keys through their whole lifecycle against loss, unauthorised access, disclosure and modification. The controls shall be designed taking into account the results of the approved data classification and the ICT risk assessment processes. |
With the MTG Key Management System (KMS), cryptographic keys can be managed and protected throughout their entire life cycle. A Hardware Security Module (HSM) is used as a security anchor so that a high level of protection of the managed keys is also guaranteed on the technical/hardware side. |
|
Financial entities shall develop and implement methods to replace the cryptographic keys in the case of lost, compromised or damaged keys. |
Certificates can be revoked centrally in the MTG Corporate PKI. In addition, the PKI provides information on the validity of certificates via revocation lists (CRLs) or online queries (OCSP). This ensures that keys from revoked certificates are not reused. All other types of cryptographic keys can be managed via the MTG KMS. This also includes the deletion and exchange of keys. |
|
Financial entities shall create and maintain a register for all certificates and certificate-storing devices for at least ICT assets supporting critical or important functions. The register shall be kept up-to-date. |
The MTG Certificate Lifecycle Manager (CLM) is a central platform for all of a company's certificates. This can be used to import and manage certificates from your PKI as well as certificates from third-party providers. A dashboard makes it possible to keep an overview of the certificates contained and to carry out evaluations. |
|
Financial entities shall ensure the prompt renewal of certificates in advance of their expiration. |
The MTG Certificate Lifecycle Manager (CLM) monitors the validity periods of all managed certificates and actively alerts you via a dashboard or e-mail when certificates are approaching the end of their validity period. |
Use cases
Article 6 of RTS JC 2023 86 requires comprehensive encryption of
- data at any time during their processing (at rest, in transit, in use) and
- Internal and external network traffic.
To meet these requirements, here are three examples of applications that can be easily realized based on MTG AG products:
Encryption of databases
The MTG Key Management System (KMS) offers a KMIP (Key Management Interoperability Protocol) interface via which keys managed by the KMS can be made available in a variety of applications and use cases. This includes, for example, the encryption of databases (such as MongoDB, Oracle (TDE), MySQL, DB2, etc.) or the encryption of data backups.
Encryption of virtual machines
Together with our long-time partner and infrastructure service provider, DARZ GmbH, we offer a VMware Encryption-as-a-Service package that allows you to encrypt your virtual machines quickly and easily. The MTG Key Management System (KMS) manages and protects cryptographic keys. The MTG KMS has been certified by VMware. Companies can use it to reliably encrypt their VMware VM with just a few clicks via their familiar vCloud Director and vCenter user interfaces. This encryption service won the 2023 Innovation Award from TeleTrusT, the IT Security Association of Germany.
Secure identities and certificate expiry monitoring
The MTG Corporate PKI with the integrated MTG CLM (Certificate Lifecycle Manager) is ideal for all use cases in which public key certificates are used. By using policies, certificates can be defined and created individually for each use case, e.g., TLS certificates for web servers, S/MIME certificates for secure email communication, or personal certificates for two-factor authentication. This offer is available as
- Managed Cloud Solution (360° Managed PKI & CLM) and as
- On-premises solution.


