Need of KMS
IT security is a process which needs to be established in each company working with sensitive data.

Tasks of a Cryptographic Key Management System (© MTG)
A suitable cryptographic key management system (cryptographic or encryption Key Management System) has to go far beyond a conventional password manager. All IT security-relevant processes in a company require proactive security support using a central approach.
The core elements of security processes are keys and certificates. During the entire key management lifecycle, an encryption key management system has to store and manage a large number of "secrets" (SSH keys, API keys, certificates, etc.). It is essential that organizations have an overview at any point in time how keys and certificates are used on their network. Many companies use a large number of keys and certificates without central control. For example, it is not known who has access to which keys or there is no dedicated role and rights management.

Each department manages its own keys and certificates. (© MTG)
If keys and certificates are not secured effectively, the company is vulnerable to attacks. It is essential that organizations have an understanding of which keys and certificates are used on the network. They need to know who has access to them and need to control how and when they are used. It is also important to have an overview of the crypto algorithms used in the organization, in order to be able to identify current insecure algorithms.
Keep Crypto Processing Costs low!
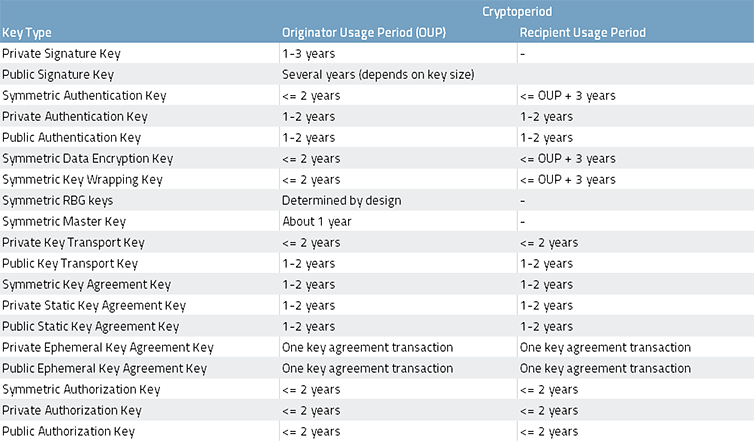
Source: Recommendation for the usage period of key material - NIST 2016
If each department will manage its own security processes, the complexity and handling costs will increase dramatically with the growing number of keys and certificates being used in different applications. Due to constant changes in security policies, obligations, strategies the security management effort is increasing. The recommendation of NIST (2016) shows, how frequently different key types should be changed to protect the systems securely. A manual process of monitoring and updating is time-consuming, increases the failure rate and causes very costly downtime risks.
Enterprise Key Management System
A central enterprise key management system (KMS) provides an overall picture of the key material used in the company. It enables controlled access to encrypted data in accordance with the IT security strategy.

A Central Enterprise KMS in an Organization (© MTG)
The administration of all keys in a central and secure location prevents unauthorized ac-cess, as well as their monitoring and control of the validity of the certificates and keys used. Against this background, a cryptographic key management system is becoming in-creasingly important and essential for the implementation of a cost-effective IT security lifecycle management.
In the company's internal infrastructure, the keys and certificates are widely distributed between different actors. These are not only machines (such as PCs), but also human participants accessing the infrastructure. The fast and easy integration of storage devices, networking devices, personal devices with embedded storage (e.g. personal computers, handheld computers, cell phones), databases etc. is therefore an important task. By using KMIP (Key Management Interoperability Protocol), the connection of different systems for cryptographic key operations is standardized by OASIS (Organization for the Advancement of Structured Information Standards). Numerous well-known companies have already integrated the KMIP protocol.
IoT Key Management System
IoT device manufacturers who process personal or sensitive data will need effective key management in the future.
Industry standards increasingly recommend the use of keys to protect smart IoT devices (e.g. OMS). Regulatory compliance will also become one of the prime influencers for IoT security uptake. For example, the European Data Protection Regulation (GDPR) will have an enormous impact on suppliers of IoT devices. In this context the GDPR asks for a pseudonymization and encryption of personal data. Violations are subject to high penalties.
Affected are, among others, manufacturers of smart meters, heating cost meters, water meters and all other “smart devices” that process personal or sensitive data. In the Internet of Things (IoT), a large number of devices communicate through network infrastructures. To protect these systems, no device may have access until it has proven that it is trustworthy. The secure identity of a device is enabled by the use of an individual, unique and secret key. Depending on the intended purpose, symmetrical or asymmetrical procedures can be used.
Consequently, each "smart device", handling with sensitive personal data, will have to receive one or more individual keys (e.g. AES keys), in order to meet the growing security and data protection requirements.
Instead of distributing a few keys across large production series, a large number of individual keys must now be generated, assigned to the individual devices and managed. Manufacturers and also their customers need to manage millions of keys and their lifecycle in many of their company processes. This faces IoT manufacturers and their customers to new challenges. Without a central KMS, the level of complexity for key management increases with the growing number of individual keys to be managed at different touchpoints from production to the delivery and operation at customer side. Various and complex security requirements cannot be implemented cost-effectively and completely in every single application. The management of keys and certificates for such applications should therefore always be done centrally.
Therefore, a central cryptographic IoT Key Management Software (IoT KMS) as developed by MTG will become indispensable to meet highest IT security requirements in IoT networks.


